Security recommendations
In order for Nerve to operate in a secure manner, there is a set of measures that need to be taken by implementers of Nerve. This section gives the necessary background information and a Security recommendations checklist containing a summary of the suggested measures.
Security context and security measures expected by the environment
It is important to understand the setting for which Nerve has been designed. All security considerations and the security certification are based on these scenarios. If Nerve is used in a different scenario, the implementers of security will have to assess the impact of the changed security context and adapt their security strategy accordingly. Note that no Nerve interface shall be exposed directly to the internet.
- Implementers of security shall ensure that no Nerve interfaces are directly exposed to the internet.
Nerve considers the machine builder and factory owner scenarios.
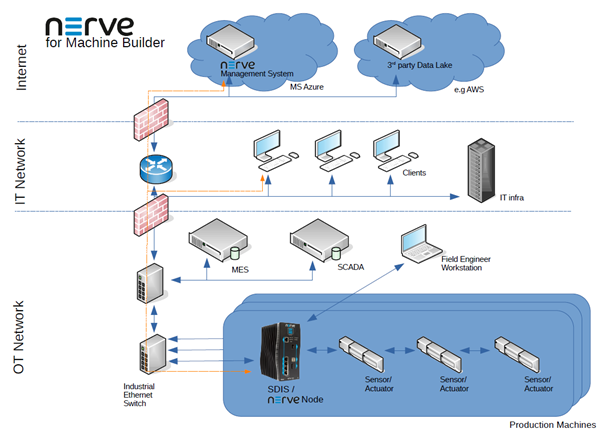
Machine builder scenario
In this scenario, Nerve is installed in a machine in a production environment and delivered as part of the machine. It is likely that the included soft PLC controls the machine through a fieldbus connected on the fieldbus interface of the Nerve device.
On one side, Nerve is connected to the machine network, especially to the sensors and actuators inside the machine. Additionally, the Nerve device is connected to the OT network on the other side. The Nerve device cannot be reached directly from the internet.
The machine is controlled by one soft PLC connected to physical sensors and actuators within the machine. The connection is based on Ethernet using a fieldbus protocol like PROFINET or EtherCAT.
The soft PLC programs (CODESYS workloads) are developed by the machine builder and installed (i.e. deployed) on Nerve using the cloud-based Nerve Management System. The soft PLC and applications running on Nerve may also be connected to a SCADA and MES system.
The Nerve Data Services software gateway, which is directly connected to the sensors and actuators and possibly to the PLC, collects data (e.g. through OPC UA, MQTT) and provides it to an application for preprocessing and then transmits the preprocessed data to higher level applications in the IT network, OT Network or in the cloud.
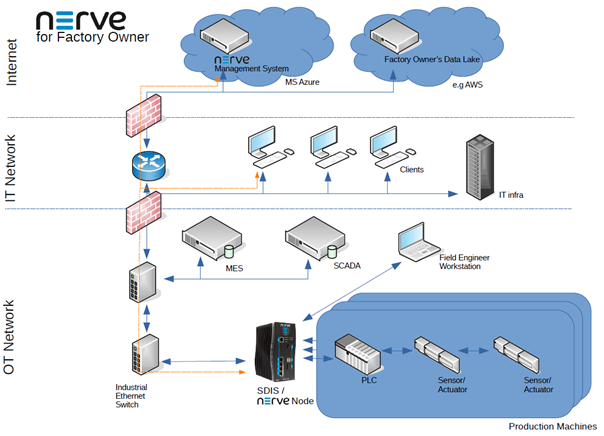
Factory owner scenario
In this scenario the factory owner installs the Nerve device in the product environment. The Nerve device is connected to the IT network and to the OT network.
The data collection scenario is similar to the machine builder use case. The Data Services gateway in Nerve is connected directly to sensors and to a PLC within the machines or production cell. The gateway, together with analytics applications executing on Nerve, process the data locally before sending it to the destination system in the OT network, IT network or in the cloud.
Defense in Depth Strategy
As per IEC62443, all compliant systems shall implement a defense in depth strategy.
For a successful implementation of a defense in depth strategy in the overall system, it is necessary for the user to understand the capabilities of Nerve and threats addressed by these capabilities.
Refer to the respective sections for more information. The mitigation strategies required by the user are summarized in the Security recommendation checklist.